Imagine for a moment a place where everything you need for your work or personal projects is kept safe, a sort of special club where only the right people get in. This place, you see, holds all your important emails, your private files, and the tools you use every day. It's a bit like having a very careful doorman who knows exactly who should be there and who shouldn't, making sure everyone who enters is supposed to be there, and doing it without making things difficult for you. This whole idea, this system that makes sure only the right folks get to see or use certain things, is a pretty big deal in the digital world.
So, when we talk about something like "iam pandoraaaa," we are really getting at the heart of how this digital doorman operates. It is about making sure that every person, or even every piece of software, that wants to get at your company's valuable stuff is first checked out. This process, which might seem a little complex at first, is actually about making your digital life smoother and much safer. It's about giving you peace of mind, really, knowing that your digital belongings are well looked after.
It's a way, too, of keeping things organized in a big digital space, where lots of people are trying to get their work done. This system, which goes by a few names, but we are calling it "iam pandoraaaa" here, is what helps keep all those digital doors locked tight, opening only for those with the right key. It is about setting up a clear path for people to do what they need to do, without letting anyone wander into places they shouldn't be.
Table of Contents
- What is iam pandoraaaa?
- iam pandoraaaa - The Digital Guardian: A Closer Look
- Why is iam pandoraaaa So Important?
- How Does iam pandoraaaa Actually Work?
- iam pandoraaaa - Keeping Your Digital World Safe
- iam pandoraaaa and its Role in Protecting Digital Identities
- What Kind of Information Does iam pandoraaaa Handle?
- Who Benefits from iam pandoraaaa in a Big Group?
What is iam pandoraaaa?
So, you might be wondering, what exactly is this "iam pandoraaaa" we are talking about? Well, it's essentially a way for digital systems to figure out who you are and what you are allowed to do. Think of it as a very careful gatekeeper for all the valuable digital things a company has. It's really about making sure that only those who should have access to certain information or tools actually get to them. This gatekeeper, you know, works quietly in the background, making sure everything runs smoothly.
It gives secure entrance to things like your work emails, company records, important facts, and software tools. This secure entrance is only for those who have been checked and approved. The main idea, or so it seems, is to let people get to what they need with the least amount of fuss possible. It's about making things easy for the right people, while keeping out anyone who shouldn't be there. This careful balance is what "iam pandoraaaa" aims for.
This whole practice of managing who is who on computers is called "identity management," or "idm" for short. It's the job of looking after all the details about people who use the computer systems. These details include things that help confirm someone is truly who they say they are, and other bits of information that relate to them. It's a bit like keeping a very detailed guest list, actually, for a very important gathering.
iam pandoraaaa - The Digital Guardian: A Closer Look
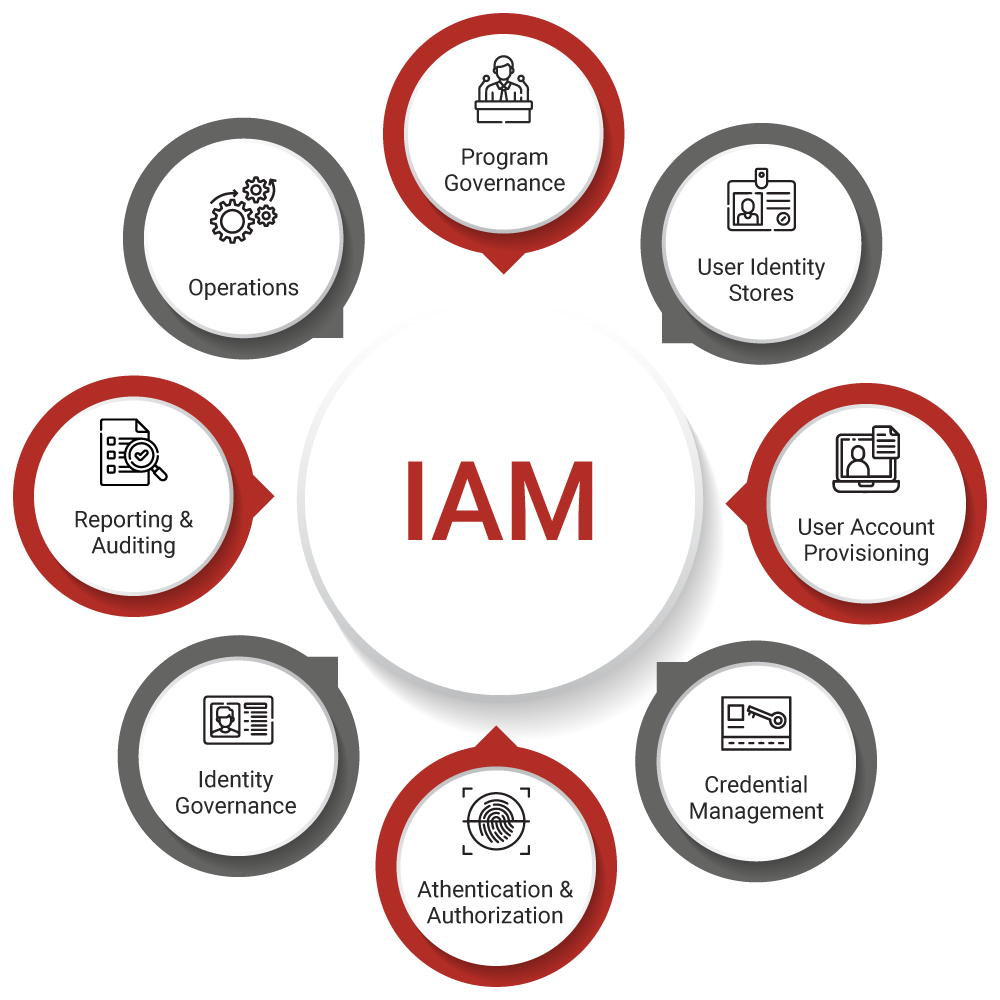
In this discussion, you will get to know some of the basic ideas behind identity and access management, which we are calling "iam pandoraaaa." You will also see why it holds such importance and how it goes about its work. It's a way, you see, of protecting your digital self and controlling who gets to use what inside a company's computer setup. This means looking after both who you are online and what doors you are allowed to open.
This "iam pandoraaaa" is a kind of overall plan and a set of ways of doing things that companies use to look after and keep safe digital identities. It also helps them control what people can get to when it comes to important information. It's about putting clear boundaries in place, so that sensitive company facts stay private and only seen by those with permission. This framework, in a way, is the backbone of digital safety for many groups.
It's a collection of rules, ways of doing things, and special tools that let companies manage who is who online and control what people can get to when it comes to important company facts. This means it helps companies figure out who is trying to get in and then decide if they are allowed. It's a continuous process, you know, that helps keep things in order and secure.
Why is iam pandoraaaa So Important?
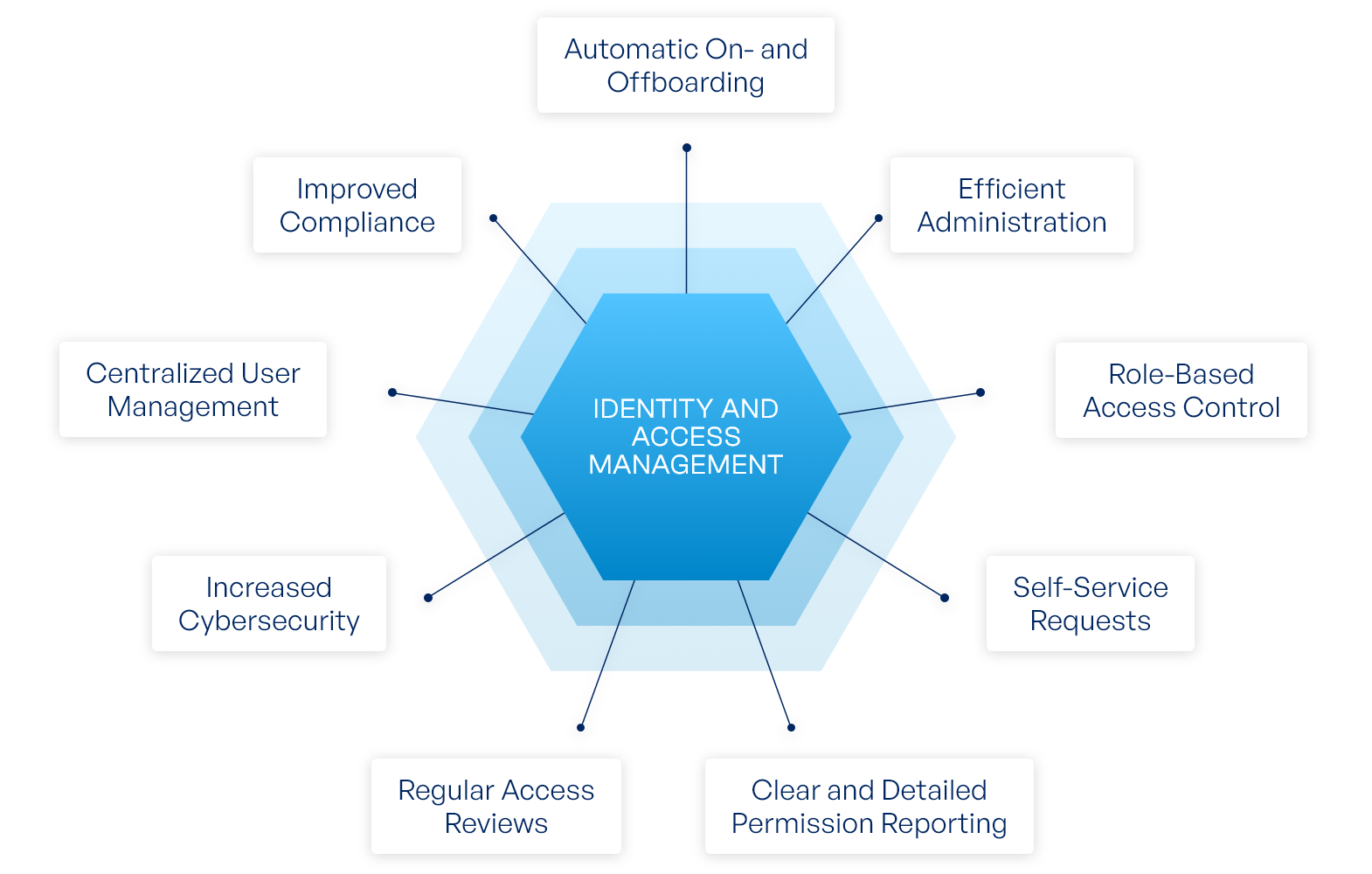
So, why does all this matter? Why is "iam pandoraaaa" such a big deal for companies? Well, think about all the valuable information a business has – customer lists, financial records, secret plans. Without a good way to control who sees what, this information could easily fall into the wrong hands. It's about protecting the very heart of a business, really. A good "iam pandoraaaa" system helps keep those secrets safe.
It's also about making sure that people can do their jobs without unnecessary hurdles, yet without letting them stray where they shouldn't. If everyone has access to everything, it becomes a mess, and security risks go way up. But if access is too tight, people can't work. "iam pandoraaaa" strikes that balance, making sure people have just what they need, and nothing more. It's a pretty smart way to handle things, actually.
The core purpose of "iam pandoraaaa" is to make sure that only approved people and devices can get to a company's valuable items. This means it acts as a very strict checker at the entrance, making sure everyone has the right papers. It's about putting a strong barrier around the things that matter most, stopping unwanted visitors from getting in. This kind of protection is, in some respects, absolutely vital for any group working with digital information.
How Does iam pandoraaaa Actually Work?
You might be curious about how "iam pandoraaaa" actually does what it does. It's a bit like a very organized system that has two main parts: knowing who someone is, and then knowing what they are allowed to do. First, it figures out your identity. Are you really John from accounting, or Sarah from marketing? It uses certain pieces of information to confirm this. This first step is, you know, very important.
Once it knows who you are, it then checks a list to see what you are permitted to get to. Are you allowed to see the sales figures? Can you change customer details? This second part is about setting the right permissions. It's a bit like giving you a special badge that says exactly which rooms you can enter in a big building. This system works quietly, making sure every request for access is checked against these rules.
This is the part of computer information work that is all about checking who users are and then managing what they can get to when it comes to digital items. It's the practical side of making sure that only the right people can open certain files or use specific programs. This process, which is quite detailed, helps keep everything running smoothly and safely. It's a very systematic approach, you see, to digital safety.
iam pandoraaaa - Keeping Your Digital World Safe
Identity and access management, or "iam" for short, is a way to tell who a user is and what they are allowed to do. It's like the careful person at the door of a special place, with a list of who is allowed inside. If your name is on the list, you get in. If it is not, then you do not. This simple idea is at the heart of how "iam pandoraaaa" helps keep things secure. It's pretty straightforward, really.
This technology provides a way to control user checking and getting to resources. It is commonly known as "iam," and this technology makes sure that only the right people can do things. It's the engine behind the scenes that powers the security of your digital space. It gives you, or rather, the people in charge, the tools to manage who can do what with valuable company assets. This control is, you know, a very good thing to have.
iam pandoraaaa and its Role in Protecting Digital Identities
This "iam pandoraaaa" system lets those in charge give permission for who can take action on specific resources. This gives you full control and a clear view to manage things like company data. It's about having a clear picture of who is doing what, and making sure that those actions are permitted. This kind of transparency is, in some respects, incredibly helpful for keeping things secure and organized.
It's a way of setting up digital permissions, almost like assigning roles in a play. Each role has certain lines to say and certain actions to perform, and "iam pandoraaaa" makes sure everyone sticks to their script. This helps prevent mistakes and, more importantly, stops any bad actors from getting where they shouldn't be. It's a bit like having a very strict stage manager for your digital operations.
What Kind of Information Does iam pandoraaaa Handle?
So, what kind of details does "iam pandoraaaa" actually look after? It takes care of information about users on computers. This includes things that help confirm a user's identity, like a username and password, or perhaps a special code. It's about the unique digital fingerprint of each person who interacts with the system. This information is, you know, the key to granting or denying access.
Beyond just confirming who you are, it also manages what you are allowed to do once you are inside. This could mean knowing that you can read certain files but not change them, or that you can use a particular program but not install new ones. It's a very fine-tuned system, actually, that sets boundaries for every user based on their role and needs. This detailed management is what makes "iam pandoraaaa" so effective.
It's about keeping track of all these digital permissions and making sure they are up to date. If someone changes roles in the company, their permissions might need to change too. "iam pandoraaaa" handles these updates, making sure that access is always current and appropriate. This ongoing management is, in a way, what keeps the digital doors working correctly over time.
Who Benefits from iam pandoraaaa in a Big Group?
When you think about big groups of people, like those in large companies or even unions, "iam pandoraaaa" plays a very big part. For instance, a very large labor union with many active and retired members uses these kinds of systems. This union, which is one of the biggest and most varied groups in North America, has members from all sorts of places. Think of people who work for big airplane makers or even those who build motorcycles. All these people need safe access to different things.
For all these different people, from folks at big manufacturing places to those who keep planes flying, "iam pandoraaaa" helps manage who gets to what. It ensures that a worker at a large airplane company can access their work schedule but not the company's financial records, unless that is part of their job. It's about giving everyone just what they need to do their work, and no more. This precise control is, you know, very helpful for big groups.
So, it's not just about keeping secrets safe; it's also about making sure that daily work can happen smoothly for a very large number of people. Imagine the chaos if everyone in a huge group could just look at anything they wanted. "iam pandoraaaa" prevents that, making sure that each person's digital experience is tailored to their role. It's about creating order in a very big digital space, which is, in some respects, a pretty remarkable feat.
The core idea is to give people the right level of access, making sure they can do their jobs without getting into areas they shouldn't. This is especially true for groups with many different kinds of workers, each needing different tools and information. "iam pandoraaaa" helps sort all that out, making sure everyone has what they need, and nothing they don't. It's a very practical solution, really, for handling access on a large scale.
Detail Author:
- Name : Dr. Micah O'Hara
- Username : birdie27
- Email : casimer76@wolf.net
- Birthdate : 1979-12-23
- Address : 557 Padberg Harbors Apt. 314 East Manuelberg, IN 81371
- Phone : +1-715-310-4819
- Company : Mills-Hayes
- Job : Sheet Metal Worker
- Bio : Optio pariatur nobis quia voluptas dicta at qui. Eveniet sint veritatis expedita ipsa dolorem. Est iusto molestias dolorem ipsum enim repudiandae. Molestiae sunt ea magnam quas eum est.
Socials
twitter:
- url : https://twitter.com/susie_real
- username : susie_real
- bio : Labore qui aut dolorem quod fuga voluptates. Autem quam aliquid consequatur. Ut non deleniti qui.
- followers : 778
- following : 195
instagram:
- url : https://instagram.com/susiemitchell
- username : susiemitchell
- bio : Sint odit nobis aut. Dolor enim sit dolorum qui eveniet ipsam id. Id quia veniam in quis vel et.
- followers : 6705
- following : 2869

